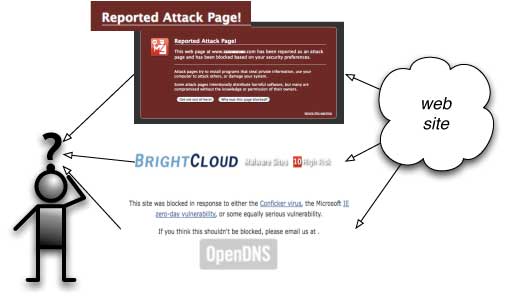
 In early June, I was in a nice rainy East Coast US city for meetings dealing with particularly thorny issues related to ways the Internet experience is being killed off for regular folks—and for institutions (NGOs) that are promoting free speech and human rights. Over a small breakfast, I sketched in my book some notes about the progression of malware over time. Basically paralleling the development I describe in my site The Social Graph of Malware, malware has gone from simple and juvenile defacement of web sites to become sophisticated and bandwidth-hogging socially-engineered schemes designed to get people to fall for a purchase they didn’t want to make, or just to click a link to enroll their computer in a network of zombies poised to conduct nasty attacks on other people.What strikes me as the next stage in targeted attacks[1] hasn’t really been spoken of much, and the attacks only began in earnest during mid-2009—it’s that I think we’re entering an era in which attacks will be positioned to create a “bad aftertaste” and thus kill off the visitor/audience for some big web sites. The attacks are, in a sense, damaging the reputation, good will, and the brand of the attacked sites. These attacks take advantage of the Google Safe Browsing interface now available in Firefox and Chrome browsers, and the (new) BrightCloud toolbar for Firefox and for Chrome—both of which alert a web user that they are about to use a web site that could contain malware [see diagram]. A would-be site visitor is presented with one of these “warnings” and is dissuaded from viewing the site. (Once the site has been cleaned up, the warning disappears, and visitors may decide to click through and go to the site anyway, if they wish.) The problem is that you are left with the bad aftertaste of having gone to a legitimate site, seen this explicit warning, and you may decide never to go back even if the warning has been removed!
In early June, I was in a nice rainy East Coast US city for meetings dealing with particularly thorny issues related to ways the Internet experience is being killed off for regular folks—and for institutions (NGOs) that are promoting free speech and human rights. Over a small breakfast, I sketched in my book some notes about the progression of malware over time. Basically paralleling the development I describe in my site The Social Graph of Malware, malware has gone from simple and juvenile defacement of web sites to become sophisticated and bandwidth-hogging socially-engineered schemes designed to get people to fall for a purchase they didn’t want to make, or just to click a link to enroll their computer in a network of zombies poised to conduct nasty attacks on other people.What strikes me as the next stage in targeted attacks[1] hasn’t really been spoken of much, and the attacks only began in earnest during mid-2009—it’s that I think we’re entering an era in which attacks will be positioned to create a “bad aftertaste” and thus kill off the visitor/audience for some big web sites. The attacks are, in a sense, damaging the reputation, good will, and the brand of the attacked sites. These attacks take advantage of the Google Safe Browsing interface now available in Firefox and Chrome browsers, and the (new) BrightCloud toolbar for Firefox and for Chrome—both of which alert a web user that they are about to use a web site that could contain malware [see diagram]. A would-be site visitor is presented with one of these “warnings” and is dissuaded from viewing the site. (Once the site has been cleaned up, the warning disappears, and visitors may decide to click through and go to the site anyway, if they wish.) The problem is that you are left with the bad aftertaste of having gone to a legitimate site, seen this explicit warning, and you may decide never to go back even if the warning has been removed!
In prior years, attacks have been positioned to “take down” legitimate businesses by denying access to their sites [DDoS].[2] Soon it was discovered (and is not widely exploited yet) that if an attacker simply hammers a site so hard that the defending organization has to dedicate more resources (read “money”) to defense, they can wear down the organization by depleting its budget and even its “will to stay alive online.” This doesn’t work if the attacker is just exploiting a site to drive traffic to its own illegitimate sales site, but it does work if the attacker’s intent is to take the organization down.
I already see evidence of small to medium attacks of the economic sort, and predict that we will see far more of them during the remainder of 2010 and 2011. I am working with NGOs now to prevent this type of “bad aftertaste” attack trend, and will report on how it’s going as I gather more information and evidence.
To get a feel for how much this is happening, see the StopBadware and the BadwareBusters web sites (forums where people are discussing these attacks and their remediation).
[1] Many attacks taking place on web site today are opportunistic rather than targeted, meaning that an attacker finds a web server that can be exploited and compromised and then uses it regardless of who it represents or affects. By and large, these attackers want to remain undiscovered, if possible, so the compromised server doesn’t get fixed any time soon. Therefore, it’s usually a “silent” attack with no immediately visible consequences on the web page.
[2] (Distributed) Denial of Service attacks bog down the target web servers so they can’t respond to legitimate requests from customers. They make it impossible to reach the business or organization. In some cases, the attacker asks for a “ransom” payment to stop the attack, is other cases they conduct a short-lived attack to make a protest or prove a point, and in some cases they continue their attack long enough to have a direct economic impact on the target.
Leave a Reply